Cyber News - Felix Krause, iOS developer and founder Fastlane.Tools demonstrate phishing attacks that are hard to detect and explains how malicious iOS apps can steal Apple ID passwords to gain access to iCloud accounts and data.
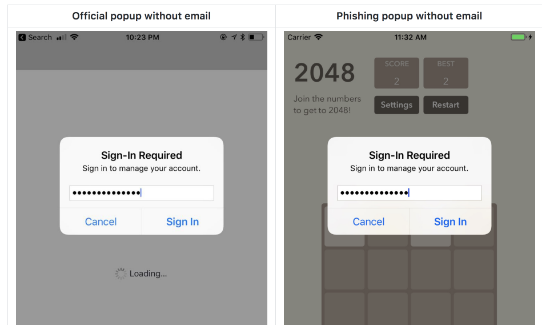
According to a blog post published on Tuesday by Krause, an iOS app can use "UIAlertController" to display a fake dialogue box to users, mimicking the look and feel of Apple's official system dialogue.
Therefore, this makes it easier for attackers to convince users to provide Apple ID passwords without suspicion.
Although there is no evidence of malicious attackers exploiting this phishing trick, Krause says that "it's easy to mimic system dialogue," which allows any malicious application to abuse this behaviour.
For security reasons, the developer has decided not to include the actual popup source code when demonstrating the attack.
Here's How To Prevent Phishing Attacks Like This
To protect yourself from these clever phishing attacks, Krause suggests users press the "Home" button as they display the suspicious box.
If pressing the Home button closes both applications, which appears, and the dialogue box is missing, then it is a phishing attack.
If dialogues and apps still exist, then it is an official system dialogue by Apple.
"The reason is that system dialogues run on different processes, and not as part of any iOS app," the developer explained.
Krause also advises users not to insert credentials into any popups and manually open the app settings and then enter the credentials there, just as users do not click on links received via email and log in to legitimate websites manually.
Most importantly, always use 2-factor authentication, even if the attacker gets password access, they still need to struggle to bypass authentication.
According to a blog post published on Tuesday by Krause, an iOS app can use "UIAlertController" to display a fake dialogue box to users, mimicking the look and feel of Apple's official system dialogue.
Therefore, this makes it easier for attackers to convince users to provide Apple ID passwords without suspicion.
Although there is no evidence of malicious attackers exploiting this phishing trick, Krause says that "it's easy to mimic system dialogue," which allows any malicious application to abuse this behaviour.
For security reasons, the developer has decided not to include the actual popup source code when demonstrating the attack.
Here's How To Prevent Phishing Attacks Like This
To protect yourself from these clever phishing attacks, Krause suggests users press the "Home" button as they display the suspicious box.
If pressing the Home button closes both applications, which appears, and the dialogue box is missing, then it is a phishing attack.
If dialogues and apps still exist, then it is an official system dialogue by Apple.
"The reason is that system dialogues run on different processes, and not as part of any iOS app," the developer explained.
Krause also advises users not to insert credentials into any popups and manually open the app settings and then enter the credentials there, just as users do not click on links received via email and log in to legitimate websites manually.
Most importantly, always use 2-factor authentication, even if the attacker gets password access, they still need to struggle to bypass authentication.

![[Learning Module] Metasploit The Penetration Tester's Guide : Basic Absolute For Penetration Testing](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjgIGcys0kl5v0lguuoTfjDFY5pdnrH_-ZKRVMSCfvaZXodh3I3Y9Ketrvqw41ekC79J1tTzJ7k6zTOlRrGgh22Q4_3csCi_FPJ9_a3NV7R9q6zhKBV-mGj8NxY2wIU7FE0Gf2sdlkx95A/s72-c/Penetration-Tester-Guide-CyberNews404.PNG)


![[Learning Module] Know Basics Metasploit Framework](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEg3Wec4enTBqy4eKBwLu8gx8WqA91QEDJ-S72f7ClITyBAj2jZX4Kj69Lqj5hGqgLp_HzeK4Zw9hYvrWrg7BssGrDetGzZnzHEvBiWN3i-Qsp6lkrCiHaj7XPKqXGQ0iVjxfzKn4u7_XZM/s72-c/Metasploit.PNG)

No comments:
Post a Comment