CyberNews404 - What do you imagine when you hear the term cybercrime? Is it direct to the figure of hackers in movies or supercomputers that can solve the entire code in all network traffic? Yes, if it's all in your mind, then it's also not wrong.
In fact, cybercrime is something quite simple, and that often becomes their goal is none other than stealing user accounts. So, protecting accounts and passwords is an obligation for all internet users. Do not use passwords that are short or easy to guess. In addition, we also need to know the most common ways that many hackers use to hack passwords so that we do not become the next victim. Want to know the reviews? Let's just see below.
7 Hacker Frequently Used Ways to Hack Passwords
1. Use Password Dictionary
The first way often used hackers to hack the victim account is to use a password dictionary. Inside the dictionary contains some of the most frequently used password combinations. So password combinations like 123456, qwerty, password, princess, it must be listed in it.
The advantage of this password dictionary is the attacker can find the victim's password very quickly because the read the dictionary database is a computer device. So from that, if your account and password want to be safe from hackers, then one way is to create a strong password and not easy to guess by anyone. Or another alternative way is to utilize a password manager program like LastPass.
2. Brute Force
Then the second way we need to be aware of is the brute force attack, which attacks focus on the combination of characters used in passwords. Keywords that are used usually in accordance with the algorithm owned by the password manager, such as a combination of several uppercase letters, lowercase letters, numbers, and some symbol characters.
This brute force attack will try some combination of the most widely used alphanumeric characters, such as 1q2w3e4r5t, zxcvbnm, and qwertyuiop. Well, are you guys including using such a password?
The advantages of this way are to increase the variation of the attack rather than just using a dictionary password only. If your account wants to be safe from brute force attacks, then use a combination of more varied characters. When possible use also extra symbols to increase password complexity.
3. Phishing
Phishing is one of the most popular ways to get victim's accounts to date. So, phishing is an attempt to trick the target so they do not realize if they are being cheated.
The phishing email is now one of the most popular ways to get victim's account, and every day there are billions of fake emails sent to all internet users around the world. The mode is that victims will receive fake emails claiming they are a trusted organization or business. Usually, the content of this email requires the victim to do something like submitting personal information and others.
In addition, fake emails also sometimes contain information that directs a target to click on a particular site link, which can be either malware or a fake website that is created similar to the original web. So, in this case, the victim is unaware if they are being directed to submit important personal information.
4. Social Engineering
Social engineering is similar to phishing techniques, but this technique is more used in real life. For example, the case of 'mama ask for credit' also uses this technique, the victim who is not aware can easily immediately believe the contents of the message and immediately follow the directive given the deceiver.
This social engineering technique has been around for a long time and this is even misunderstood as a method to deceive victims indirectly, such as asking for a password or asking for some money.
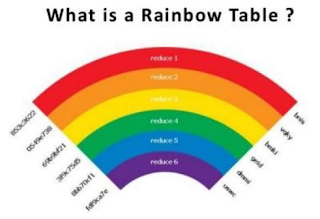
5. Rainbow Table
Rainbow table is a form of attack by utilizing the database of accounts and passwords that have been obtained. In this case, the attacker already pocketed the list of the target username and password but in the form of encryption. This encrypted password has a very different view of the original, for example, the password obtained is 'Jalantikus', then its MD5 hash encryption form is "8f4047e3233b39e4444e1aef240e80aa", is not it complicated?
However, in certain cases, the attacker simply runs a list of plaintext passwords through a hashing algorithm and then compares the result with the password data that is still in the form of encryption. Yes, arguably not one hundred percent secure encryption algorithm and most of the encrypted password was still easily broken.
This is why the rainbow table method is most relevant today, instead of attackers having to process millions of passwords and match the hash values it generates, the rainbow table itself is already a hash list of previously calculated algorithms.
This method can reduce the time it takes to break the target password. Well, hackers themselves can buy a rainbow table that has been filled with millions of potential password combination and widely used. So, avoid sites that still use the SHA1 or MD5 encryption method as a hashing password algorithm because this method has found security holes.
6. Malware / Keylogger
Another way that can harm your account and important information on the internet is because of malware or malicious programs. This malware has spread throughout the internet network and has the potential to continue to grow. The danger again if we get exposed to malware in the form of keylogger, then unconsciously every activity we in the computer can be known by the attacker.
This malware program itself can specifically target personal data, then the attacker can easily control the victim's computer remotely to steal any valuable information.
For those of you who do not want to get malware, then never use pirated apps. Then do not be lazy to update antivirus and antimalware software available. Also always be careful while browsing the internet and do not origin download files from sources that are not clear.
7. Spidering
Spidering is a technique for finding information by searching for various clues or a series of data related to the target. Attackers can start by searching for personal data and compiling them to be assembled into valuable information. This method is commonly referred to as spidering techniques or searching the spider web.
Therefore, do not create usernames and passwords related to personal information, such as birth date, spouse's name, pet's name, and so on that relate to our data. This is because the information is very easy to guess and traceable.
These are the most common ways hackers use to hack passwords. In essence, there is no one hundred secure method to protect our important accounts from hacker threats. However, the best thing is we can still reduce the threat by knowing the common ways that hackers often use to steal our account and password. Maybe useful.








![[Learning Module] Metasploit The Penetration Tester's Guide : Basic Absolute For Penetration Testing](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjgIGcys0kl5v0lguuoTfjDFY5pdnrH_-ZKRVMSCfvaZXodh3I3Y9Ketrvqw41ekC79J1tTzJ7k6zTOlRrGgh22Q4_3csCi_FPJ9_a3NV7R9q6zhKBV-mGj8NxY2wIU7FE0Gf2sdlkx95A/s72-c/Penetration-Tester-Guide-CyberNews404.PNG)


![[Learning Module] Know Basics Metasploit Framework](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEg3Wec4enTBqy4eKBwLu8gx8WqA91QEDJ-S72f7ClITyBAj2jZX4Kj69Lqj5hGqgLp_HzeK4Zw9hYvrWrg7BssGrDetGzZnzHEvBiWN3i-Qsp6lkrCiHaj7XPKqXGQ0iVjxfzKn4u7_XZM/s72-c/Metasploit.PNG)

★COMPOSITE HACKS★
ReplyDeleteAre you looking for the best Legit Professional Hackers online?
Congratulations Your search ends right here with us.
COMPOSITE HACKS is a vibrant squad of dedicated online hackers maintaining the highest standards and unparalleled professionalism in every aspect.
We Are One Of The Leading Hack Teams in The United States With So many Awards From The IT Companies. In this online world there is no Electronic Device we cannot hack. Having years of experience in serving Clients with Professional Hacking services, we have mastered them all. You might get scammed for wrong hacking services or by fake hackers on the Internet. Don't get fooled by scammers that are advertising false professional hacking services via False Testimonies, and sort of Fake Write Ups, Most Of Them are Fake Hackers/scammers and They are Always Detected Here By Signal-Arnaques.
COMPOSITE HACKS is the Answers to your prayers. We Can help you to recover the password of your email, Facebook or any other accounts, Facebook Hack, Phone Hack, you wanna monitor your kids/wife/husband/boyfriend/girlfriend, You Wanna Hack A Website or Database? You wanna Clear your Criminal Records?? Our Team accepts all types of hacking orders and delivers assured results to alleviate your agonies and anxieties. Our main areas of expertise include but is never confined to:
Website hacking, Facebook and social media hacking, Database hacking, Email hacking, Phone and Gadget Hacking, Clearing Of Criminal Records and many More
We have a trained team of seasoned professionals under various skillsets when it comes to online hacking services. Our company in fact houses a separate group of specialists who are productively focussed and established authorities in different platforms. They hail from a proven track record and have cracked even the toughest of barriers to intrude and capture or recapture all relevant data needed by our Clients.
COMPOSITE HACKS understands your requirements to hire a professional hacker and can perceive what actually threatens you and risk your business, relationships or even life. We are 100% trusted professional hacking Organization and keep your deal entirely confidential. We are aware of the hazards involved. Our team under no circumstances disclose information to any third party. The core values adhered by our firm is based on trust and faith. Our expert hacking online Organization supports you on time and reply to any query related to the unique services we offer.
COMPOSITE HACKS is available for customer care 24/7, all day and night. We understand that your requirement might be urgent so we have a separate team of allocated hackers who interact with our Clients round the clock. You are with the right people so just get started.
CONTACT US TODAY: compositehacks@gmail.com.