CyberNews404 - Guess what's more expensive than fake United States passports, stolen credit cards and even weapons on the Dark Web? The more expensive one is the certificate of signing the digital code.
A study by the Cyber Security Research Institute (CSRI) this week revealed that a certificate of stolen digital code signing is available for anyone to purchase on Dark Web for $ 1,200.
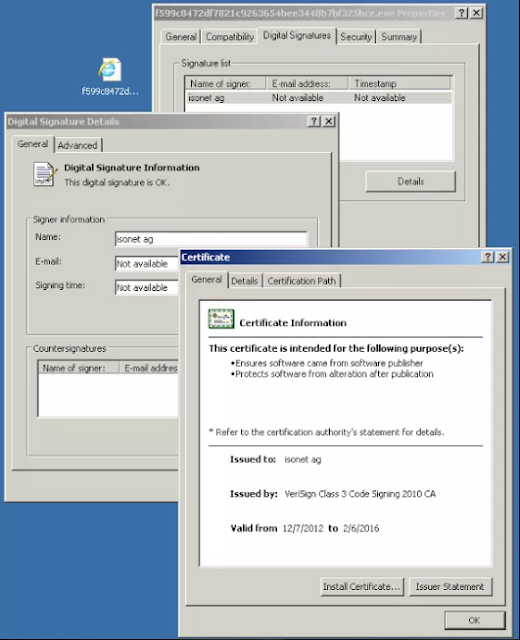
As you know, digital certificates issued by a trusted certificate authority (CA) are used cryptographically to sign applications and computer software and are trusted by the computer for the execution of the program without warning messages.
However, malware and hackers who are always looking for advanced techniques to bypass security solutions have been misusing trusted digital certificates over the past few years.
Hackers use digital signing code certificates that are compromised, associated with trusted software vendors to sign their malicious code, so their malware possibilities are not detected in the corporate network and targeted consumer devices.
The famous Stuxnet worm targeted Iran's nuclear processing facility in 2003 also used a legitimate digital certificate. Also, recent infection downloads by CCleaner are possible due to digitally signed software updates.
More Digital Signed Malware
However, separate research conducted by the security research team found that digitally signed malware has become much more common than previously thought.
The trio researchers - Doowon Kim, BumJun Kwon and Tudor Dumitras from the University of Maryland, College Park - said they found a total of 325 signed malware samples, of which 189 (58.2%) carry valid digital signatures while 136 carry digital signatures wrong.
"The wrong signatures are useful to enemies: we found that simply copying Authenticode signatures from valid samples to unmarked malware samples can help AV detection bypass malware," the researcher said.
A total of 189 correctly signed malware samples were generated using 111 compromised unique certificates, issued by CA and recognized and used to sign legitimate software.
At the time this article was published, 27 of these compromised certificates have been revoked, although malware signed by one of 84 unrevealed certificates is still reliable for carrying a trusted time stamp.
"Most (88.8%) malware families rely on one certificate, indicating that the rough certificates are mostly controlled by malware creators rather than by third parties," the trio researcher said.
The researchers have released a list of rough certificates at signedmalware.org.
Revoking a Stolen Certificate Will Not Immediately Stop Malware
Even when signatures are invalid, the researchers found that at least 34 anti-virus products failed to check the validity of the certificate, which eventually let the malicious code run on the targeted system.
The researchers also conducted an experiment to find out if wrong signatures can affect anti-virus detection. To demonstrate this, they downloaded 5 unregistered random samples and virtually all anti-virus programs detected as malicious.
The trio then retrieves two expired certificates that have previously been used to sign legitimate software and malware and then use it to sign each of the five ransomware samples.
Top Antivirus Failed to Detect Malware Signed With Stolen Certificate
When analyzing the ten newly produced samples, researchers found that many anti-virus products failed to detect malware as malicious software.
The top three anti-virus products - nProtect, Tencent, and Paloalto - detect non-signed ransomware samples as malware, but consider eight out of ten samples made as secure software.
Even popular anti-virus engines from Kaspersky Labs, Microsoft, Trend Micro, Symantec, and Comodo, failed to detect some of the known harmful samples.
Other affected anti-virus packages also include CrowdStrike, Fortinet, Avira, Malwarebytes, SentinelOne, Sophos, TrendMicro and Qihoo, and others.
"We believe that the inability to detect software samples is due to the fact that the AV takes into account digital signatures while filtering and prioritizing the list of files to be scanned, to reduce overhead costs imposed on user hosts," the researchers said.
"However, the incorrect Authenticode signature check application in many AVs gives the malware authors an opportunity to avoid detection with a simple method."
The researchers said they reported the issue to the affected antivirus company, and one of them had confirmed that their product failed to check the signatures correctly and that they had planned to correct the problem.
The researchers presented their findings at a Computer and Communications Security (CCS) conference in Dallas on Wednesday.
For more detailed information on this research, you can proceed to their research paper entitled "Certified Malware: Measuring Breaches of Trust in the Windows Code-Signing PKI".

![[Learning Module] Metasploit The Penetration Tester's Guide : Basic Absolute For Penetration Testing](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEjgIGcys0kl5v0lguuoTfjDFY5pdnrH_-ZKRVMSCfvaZXodh3I3Y9Ketrvqw41ekC79J1tTzJ7k6zTOlRrGgh22Q4_3csCi_FPJ9_a3NV7R9q6zhKBV-mGj8NxY2wIU7FE0Gf2sdlkx95A/s72-c/Penetration-Tester-Guide-CyberNews404.PNG)


![[Learning Module] Know Basics Metasploit Framework](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEg3Wec4enTBqy4eKBwLu8gx8WqA91QEDJ-S72f7ClITyBAj2jZX4Kj69Lqj5hGqgLp_HzeK4Zw9hYvrWrg7BssGrDetGzZnzHEvBiWN3i-Qsp6lkrCiHaj7XPKqXGQ0iVjxfzKn4u7_XZM/s72-c/Metasploit.PNG)

No comments:
Post a Comment